
I have a Sandisk Cruzer Micro USB thumb drive that I carry around with me. Last weekend I spent a bit of time setting it so that all my data is securely encrypted using the excellent open source software called
TrueCrypt. I also managed to get Windows autoplay working on the drive so I can access the data with the least amount of annoyance. Actually it's about as easy as it's ever going to get. I stick my drive in, an autoplay menu pops up with "Mount Truecrypt Volume" as the default choice, I hit enter, type my password, hit enter again and that's it. Here's how I did it.
Requirements
- TrueCrypt. Download here.
- Windows XP with Service Pack 2. Prior to SP2 you couldn't do autoplay on removable drives. You can do everything else described here though.
- A USB thumb drive. No special requirements. Any old one will do.
TrueCrypt files
- Move all your data off your usb drive so it's empty.
- Install TrueCrypt on your PC.
- From the TrueCrypt application directory (usually C:\Program Files\TrueCrypt\) copy TrueCrypt.exe to your usb drive.
- From your Windows drivers directory (probably C:\Windows\system32\drivers\) copy truecrypt.sys to your usb drive.
Note: The TrueCrypt download is a zip file. Inside the zip file is
a folder called Setup Files that contains both TrueCrypt.exe and truescrypt.sys
so it's possible to skip steps 2, 3 and 4 above and just copy the two files
straight from that folder to your flash drive.
Autorun file
Creating the encrypted volume
- Run TrueCrypt from your start menu and click "Create Volume".
Note: If you didn't bother to install TrueCrypt in step 2, you can just double click TrueCrypt Format.exe in the Setup Files folder.
- Choose "Create a standard TrueCrypt volume" (the default).
- Type L:\data.tc at "Volume Location" where L is the drive letter of your flash drive.
- Choose your favourite encryption algorithm. (Don't ask me!)
- Select a volume size. This is how much space you will have on your encrypted volume.
I like to make it fill the entire remaining space on the thumb drive. You make it fill it exactly by doing this:
- Get the free space in bytes of your flash drive by right clicking it in My Computer and clicking "Properties".
- Divide this number by 1024 to get kilobytes.
- Back in TrueCrypt, select KB and type the number.
- Make up a password and enter it. Remember your password because there is no way to crack it. That's the point of secure encryption.
- Wiggle your mouse a bit for extra randomness, then click "Format".
- When formatting is finished click "Exit" to exit.
- This concludes the setup process. The hard part is now over!
Usage
- Remove your thumb drive in the usual way. (Click the "Safely Remove Hardware" icon in your Systray, select the drive to remove, then yank it out).
- Put it back in again. If the autoplay stuff is working you should see this:
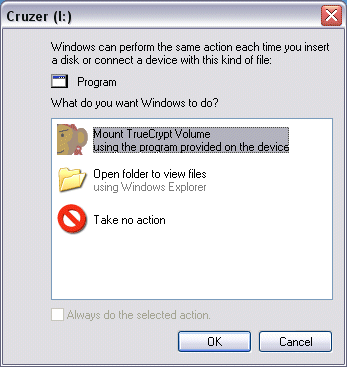
- Click OK. You should then see this:
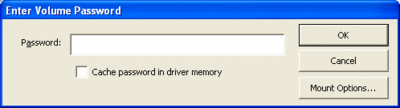
- Enter your password and up comes your encrypted drive. Voila!
- You can now put all your files back on it. They are now securely encrypted and can't be accessed without your password.
- To dismount
- Go to My Computer. Right click on your flash drive icon.
- Notice the menu options include Mount, Autoplay, Dismount and Run TrueCrypt.
- Choose Dismount to dismount the volume.
- Other notes
- Note that to open your flash drive now you have to right click and choose Open because a double click will run the Mount shell extension.
- You can also mount and dismount and change your password from the TrueCrypt program on your thumb drive. Read the TrueCrypt manual for more information.
Note: If you come to a PC where your chosen drive letter is already taken you can run TrueCrypt manually and mount your drive with a different drive letter.
- You can backup all your secure data just by copying your data.tc to your C: drive.
- I recommend adding a shortcut (to your real drive, not the virtual one) to your Quick Launch Bar for convenience. You can then access the right click menu from the shortcut.
Update 4-Nov-2005
Since I wrote this version 4.0 of TrueCrypt has been released with a whole load of great new features and improvements. As yet I have not tested the new version with the above procedure, but it should work.
Update 7-Feb-2006
Here are a couple of notes from commenters below. You have to have Adminstrator privilege on the Windows XP to mount. This probably prevents you accessing your data in internet cafes and student labs. When I wrote this I hadn't discovered the "Traveller Mode" section in the TrueCrypt manual. Read that to see how TrueCrypt can set most of this stuff up for you automatically!
Update 16-Feb-2006
Remora USB Disk Guard might be worth trying. It doesn't require that you have Administrator privilege. Found it
here.
Update 28-Feb-2006
This article was recently featured at
MakeZine. Welcome MakeZine readers! Also made it to del.icio.us popular.
Update 27-Apr-2006
I have upgraded to TrueCrypt 4.2 and everything still works except that:
- There is now a second .sys file you should probably include called truecrypt-x64.sys
- TrueCrypt now wants to store some data in Configuration.xml on your thumb drive so you should leave a little bit of space on the drive instead of filling it exactly as described above. (The xml file is about 4kb but I decided to leave an extra 1MB of free space to be sure).
Update 15-June-2006
I gave
Remora USB File Guard a try. I'm not saying it's bad product but from a useability perspective it doesn't compare to using TrueCrypt as described above. Here's what you do to edit your "secure" data using this product. Insert your thumb drive and open it up the root folder. Double click the remora exe file. Type your password. You get a winzip style of application window. Click on your file. Click export. Choose where you want to export to. Now it decrypts the file and puts it in the folder of your choice. (By the way now your data it is completely in the clear). When your done with it you then go back to remora and import it back. Then make sure you delete it from where ever it was. (Actually maybe there is an import and delete function, I didn't hang around long enough to find out). The inconvenience of this process is enough to render it useless to me. I'd rather leave my bank details unencrypted than go through that every time I needed them. In comparison the TrueCrypt solution encrypts your data on the fly. Once it's mounted you have a fully secure virtual drive. Use it like a drive. Dismount when you're done.
Update 26-July-2006
Someone asked about removing this once it's installed. It's quite simple. Here's what to do:
- Mount your encrypted drive
- Copy your stuff off it to your C: drive or whatever
- Dismount your encrypted drive
- Delete everything from your thumb drive (ie the truecrypt files and your data.tc file)
- Copy your stuff back to your thumb drive
 I have a Sandisk Cruzer Micro USB thumb drive that I carry around with me. Last weekend I spent a bit of time setting it so that all my data is securely encrypted using the excellent open source software called TrueCrypt. I also managed to get Windows autoplay working on the drive so I can access the data with the least amount of annoyance. Actually it's about as easy as it's ever going to get. I stick my drive in, an autoplay menu pops up with "Mount Truecrypt Volume" as the default choice, I hit enter, type my password, hit enter again and that's it. Here's how I did it.
I have a Sandisk Cruzer Micro USB thumb drive that I carry around with me. Last weekend I spent a bit of time setting it so that all my data is securely encrypted using the excellent open source software called TrueCrypt. I also managed to get Windows autoplay working on the drive so I can access the data with the least amount of annoyance. Actually it's about as easy as it's ever going to get. I stick my drive in, an autoplay menu pops up with "Mount Truecrypt Volume" as the default choice, I hit enter, type my password, hit enter again and that's it. Here's how I did it.
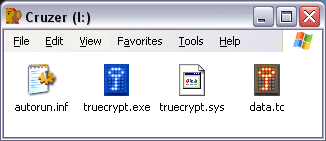 ...except for the file
data.tc. That's the file that will contain all your encrypted files that we
will create next.
...except for the file
data.tc. That's the file that will contain all your encrypted files that we
will create next.

61 comments:
I just discovered this page which is a guy who did almost the same exact thing! His page has more TrueCrypt screenshots and some extra explanations. So check it out also.
Actually he didn't include the shell extention to do right click Mount and Dismount. Instead he uses a couple of batch files.
This is great!
I wanted to keep the various TrueCrypt stuff out of the root of my USB drive, so I set up these dirs:
F:\insecure
F:\insecure\TrueCrypt
F:\insecure\TrueCrypt\(.exe, .sys here)
F:\insecure\(other non-encrypted stuff)
F:\secure\
F:\secure\(data.tc in here)
It took a few gos to work out what the paths should be in the autorun.inf: the trick was to use paths like this:
open=insecure\TrueCrypt\truecrypt /v secure\data.tc /lz /q /a /e
..they are specified from the root dir of the USB drive, but they don't start with a slash! Once I realised that it was all sweet.
Cheers
Daniel
Awesome, thanks so much for the detailed instructions. I will put my new PQI Intelligent Shtick to good use now. (Damn, that thing cost only $50.00 plus shipping at newegg.com for 1GB and it is SUPER small).
I wish newegg.com delivered to Aus. Price for 1 gig here still over $100. Dropping fast though.
You can setup this up in graphical interface available in the main window of TrueCrypt under 'Tools --> Traveller Disk Setup ...' You can also read the article 'Traveller Mode' in the user guide for more info.
TrueCrypt sounds like a great product, but not realy sure if it is the best option for a thumb drive tha you intend on using for traveling (using it at hotels and internet cafes). it's documentation indicates that when using it Travel Mode, you need to have ADMINISTRATOR privalages on the computer you are running it on, or else you will not be able to access your encrypted files.
Maybe it's my crappy PNY thumbdrive, but I keep getting corruption inside by truecypt volume.
gpg is a more flexible (but less pretty) solution.
it'll run on win95 upwards, with no admin account needed. also it's a lot stronger crypto.
Have you tried to run any of the portable apps (http://portableapps.com/) from your encrypted volume? I'm worried that the real-time encryption might slow down the apps?
Granted, I could test this myself, just wondering what YOUR experience has been?
Works good, thanks
>>"Have you tried to run any of the portable apps (http://portableapps.com/) from your encrypted volume? I'm worried that the real-time encryption might slow down the apps?"
Actually, I have noticed quite a marked effect of an increase in speed when using portable applications. I'm not sure if the read/writes are cached in memory or what, but setting it up this way increased the speed of these applications markedly -- in the case of Portable Firefox, over 400%.
cheers
What is the best way to deal with a machine that has autoplay turned off? Do you just run TrueCrypt.exe and moutn the volume that way?
Just answered my own question for what to do if Autorun is turned off.
I created 2 batch files: start.bat and stop.bat and put them in the root of my tumbdrive.
start.bat has the following entry:
TrueCrypt\TrueCrypt.exe /q /a /lZ /e /m rm /v "data.tc"
stop.bat has the following entry:
TrueCrypt\TrueCrypt.exe /q /dz
Seems to work just fine. Note (to anyone who may try this) that I have my TrueCrypt files in a subdirectory called truecrypt.
Scott, the batch file technique is a good one. I tend to use the right click/Run TrueCrypt shell extension, then use the gui.
Kaufman, I don't run any apps except putty and TiddlyWiki but I've never noticed any slowness. Note that you can choose from many encryption algorithms. Probably some are faster than others.
this seems great! but i use remora usb disk guard. and i couldnot use the autorun. could anyone please help? if possible, please reply at my email ID.
i forgot to give my email ID. it's amazingronit@aim.com
Once installed, is there anyway to remove it or am i stuck with it now?
When I run the program using TrueCrypt 4.2, I get an error that the service has ben marked for deletion, and then it closes down.
While it's fine that everyone suggests other alternatives like gpg and remora this is not the point of the article. Anyway, TrueCrypt has the advantage over most other options due to the following:
- It's free
- Simple, GUI interface, no CLI needed
- Runs on multiple platforms (Win,Lin,Mac)
- it can be made fairly portable easily
Anyway, nice article, thanks.
Tachyon
What would happen if windows hung, or the user absent-mindedly just pulled the memory stick out, or for some other reeason did not cleanly "dismount all" from within TrueCrypt?
Would all data on teh drive then be scambled?
I'm not an expert but check the FAQ at truecrypt. It mentions you can repair damaged file systems with 'chkdsk'.
I love you. Simple guide, well written, excellent! :)
>> Actually, I have noticed quite a marked effect of an increase in speed when using portable applications.
This is most likely because Windows' handling of pendrive filesystems is braindead. I still don't understand why, but when Windows writes a directory entry to a pendrive, it rewrites the entire directory table. So writing files is sloooow.
But if you use TrueCrypt, you never touch the directory structure of the pendrive - it all happens inside one file, which then has its own filesystem. The encrypted filesystem doesn't have the entire directory table rewritten on each write, so it's much faster, even though the data is encrypted on the fly.
If you want to check this, try copying various sets of data to an unencrypted pendrive. Note the the transfer rate is proportional to the average file size; the more small files, the slower it goes.
I had noticed that it can be extremely slow copying files to usb drives but I didn't know why. Thanks for the info. It's another reason to use TrueCrypt.
Three comments:
"Runs on multiple platforms (Win,Lin,Mac)"
1) Really? The TC homepage it says nothing about an existing Mac OS X version, only that one is in the works at some point. Has someone managed to get TC to compile and run on OS X? If so, please post the instructions!
2) If I plug my TC-encrypted USB stick into some random computer, is there anything to stop the owner of that system from employing a keylogger to grab my passphrase as I type it, and then just "vacuum" a copy of the contents of the stick onto the machine while it's plugged in (decrypting it in the process, of course, thanks to having the passphrase)? I don't really see any way of protecting against something like this, even theoretically.
3) [tinfoilhat] I've read the TC pages carefully and everything looks very, very solid, but the names and identities of the people currently working on / maintaining the project are conspicuously absent. Other than the kudos to the various researchers responsible for the algorithms implemented in TC (listed here) and the occasional mention of someone responsible for re-coding a module here and there, who is the TC Foundation? Just because they have a GPG key doesn't prove they're not, say, the NSA or something...[/tinfoilhat]
In any case, thanks for the excellent tutorial!
/HJ
Hate to respond to my own post, but there is a way to partially protect against keyloggers -- see the section on keyfiles in the TC documentation.
What is less clear to me is, what good would a keyfile do on a removable USB stick? If the keyfile is stored on the stick, then knowing the passphrase is enough to unlock the contents. If not (e.g. it's stored on a user's desktop at home), then you can't decrypt the contents anywhere but at home, which sort of defeats the purpose of having a removable USB drive.
Can anyone shed some light on this?
/HJ
I don't have any experience with TrueCrypt because the only encryption product that I ever used for my usb flash drive is Portable Vault. It has a drag and drop interface and installation was straight forward and simple. The 256 Blowfish encryption algorithm gives me the piece of mind that no one will be looking at my data. I highly recommend this product for encryption.
Great article! I have a very similar script available on this page which uses the WScript component to start TrueCrypt rather than pop up a DOS box in the background.
Do you have to manually un-mount the drive in XP? or can you just pull it. If manual, how critical is it, lets say the drive gets pulled by accident will my encrypted data get corrupted.
does anyone know how to make this work on Windows Vista. This works for XP but due to the fact that truecrypt requires admin rights (and the pain of have the UAC on), it just won't let me run truecrypt this way.
Everything here worked perfectly except the autoplay would only work when I used an icon that's embedded in an exe or a dll. If I used an ico file, it wouldn't autoplay. Just thought this might be helpful for some people with this same problem. Also, icon number 47 in shell32.dll is a good one.
I need some help. I encrypted the entire volume of my flash drive which i did not want to do, can someone tell me if theres a way to re-format the drive so its not encrypted? I need to do this so theres a partition on the drive that i can install the truecrypt program on.
See above under Update 26-July-2006
Great article. i found when using the above method, the autorun of the mounted volume still works! Except for the icon...
Also, when you change the autorun.inf file of the mounted volume, these changes seem to not to be used.
To make this work you'll need:
1. Mount the encrypted volume manually
2. Copy a new copy of the truecrypt.sys file from the windows directory
Great Article, and thanks for your help! Its much appreciated...Would love an autodismount via portable apps but hey....can't have everything
This is not so good of a tutorial.
Of course, if you are a programmer, it would be easy, but I am not a programmer.
I use a 128 MB Hard drive and I wanted to encrypt only 64 MB of the 128 MB.
Not being a programmer, I copied the autorun.inf, and I followed the tutorial.
Now I cannot access the remaining 64 MB.
Is there a way to do that?
Thanks!
Gabriel Mehedinti... Right Click on The USB Flash Drive and Select Explore.
/HJ has a couple valid points...
I've tried to contact the TrueCrypt staff a couple times now myself and those yella bellies never follow up! JUST like the NSA! ;P
As far as the paranoia of someone "vacuuming" the volume while keystroke logging... pretty far fetched but very possible! I've wondered that myself and came to this conclusion: "Don't stick your pepe in the glory hole."
* If you don't want your data stolen then don't insert your USB/key drive.
* If you don't want your password(s) stolen then don't touch the keyboard.
If they want it bad enough, they'll get it. Trust me.
Accessing anything that requires authentication using a computer that does not belong to you is flat-out stupidity (cyber cafe, pay-per-use computers, ect... ect...). Period. If you want to ignore this advice and use your USB/key drive anyway then just pay very close attention to your activity LED. That's what it's for. (assuming your USB/key drive has one of course)
Speaking of! Some of these pay-per-use cafe computers are scary business! Port-scan one and you'll see what I'm talking about. Most of the public computers I've played on have just about every possible privilaged/unprivilaged port wide open (hopefully because of IDS software). A lot of these machines didn't allow devices or media to be directly connected which is good... I guess.
Indeed everyone should be made aware of this possibility because I can foresee it becoming a major problem down the road when everyone is blindly walking around, poking their drives in strange places and mounting their private stuffs. =P
-Jeff
Hej.
This is really a good tutorial. Something you can use and something you need in a modern mobile world. :)
@gabriel mehedinti
This IS a good tutorial and you don´t have to be a programer to understand this tutorial.
Only a open mind is needed. But let me say these words:
Do you drive a car when you can not drive? Do you try to jump out of a driving cat, when you are not a stunt-man? No! Because you now what you can and what not.
So the problem is, that many many poeple have a computer and try really all things and what to be "good" or "special" but they have no idea of what they do. They have no knowledge of computers. So on normal cases they never have to touch a keyboard. So open your mind and try to learn some things and try to do things by yourself. Only when you do and try it yourself you can learn. Only to criticise is quite simple, TO SIMPLE.
===> But I have a QUESTION to all others.
I try the explained things above out and it worked quite simple. I now truecrypt for a longer time so it was really fast done (so fast the usb-stick is ;) ).
So I have one last problem. I put in my stick, the autorun works fine, I choose to open the encrypt truecrypt-file and it will mount. All fine.
But I also have a autorun.inf inside the encrypt-file (from the portable apps I installed there). The problem is now, that the portable apps after I mount the encrypted-file will not start automatically. The autorun.inf is not started from the mounted file and so I also have no label for the mounted drive.
That´s a little bit pitty because I thought it must work.
But I try now for a few hours, try some truecrypt-options (mount as removeable drive or not) and also try to change the autoplay functions from windows for removable-drives (it is activated all the time) but it does not work!
I also can´t choose "Auto play" from the context menu of the mounted truecrypt-file(drive).
That´s really pitty. It´s not really nice to always start automatically the portableapps.exe and does not have a volume label.
Has someone try this out and worked it?
I must know if it workes generally so I keep up trying. ;)
Greetings from Germany
/Thrash
Ps.:
If you try to contact me:
thrash at gmx dot net
Thrash, I've tried that (autorun.inf on the virtual drive) but it didn't work for me either.
great technical stuff.... thanks a lot
@simon
Thanks! What a pitty ... but it is also easy to use. Security will always be a little bit laborious.
TrueCrypt now works with Mac as well.
I have a problem on Vista...seems it looks for my .tc-file in C:\WINDOWS\System 32\ instead of on the root of the thumb drive. I guess some changes in autorun.inf is the solution, but I don't know what those changes are...Help? Please? Pretty please? :)
Why does this sound so complex? I just want a drive that asks me for my password once every time I put it in the computer. Don't see much use really, I mean if you have info worth protecting then it can be cracked. A good reason would be to retrieve your drive when you misplace it in class the next day with the knowledge that no one has viewed all your files.
It's great and it works but...what if my flash drive is 8gb?
Cracking program, cracking post nuff said.
Britec - www.britec.org.uk
Thanks for your post. Truecrypt is running perfectly on my 160Gb 2.5 inch portable drive. However, is it possible to autorun a program (e.g. Portable Apps) from the mounted volume? I can't get it to work.
You should also try SanDisk and McAfee’s new secure USB drive Cruzer Enterprise with anti-malware protection from McAfee. This is really a great solution for our company. Read more at: http://www.sandisk.com/enterprise
I have just done it with the 6.1a Version of Truecrypt and its working. The only problem I'm having is that my USB is 16GB and can only be formatted wit FAT32 so I cannot create a volume bigger than 4GB. I also have the problem of trying to use my drive in a computer without administrator rights and it's not working. Have you found a workaround?
To convert a volume to NTFS from the command prompt
1.
Open Command Prompt. Click Start, point to All Programs, point to Accessories, and then click Command Prompt.
2.
In the command prompt window, type: convert drive_letter: /fs:ntfs
i still dont know how to use it.
can someone teach me
I have to say this tutorial is awesome.
Just to add a little bit
the /a is redundant in the command line
also you can "autorun" off of the encrypted volume by having the action in autorun.inf point to a batch file (crude I know) instead of the command (i think Thrash was asking about this)
for example I am using the encrypted volume for backup so I am having it run backupkey.exe off of the encrypted volume after mount
autorun.inf:
[autorun]
label=Cruzer
icon=truecrypt.exe
action=Mount TrueCrypt Volume and Begin Backup
open=backup.bat
(the rest is the same)
and then
backup.bat:
truecrypt /v data.tc /lz /q /m rm
z:\backupkey.exe
have fun!
also truecrypt.org has great info if you need more help or tutorial
Thank you so much for this tutorial!
This is amazing, I used it to protect my thumbdrive. So much more conventient than to use the Truecrypt "portable mode".
I do have one concern though: that somebody may delete the data.tc archive by accident.
I nested my TC files deep within a "Private" folder and marked the files "Hidden", but the concern remains.
How about if the autorun command would automatically make the data.tc file read-only (unless it already is), and remove the read-only attribute just before launching the "Mount with Truecrypt" command? Would that be feasible?
To the previous poster: Partition your drive (one small unencrypted FAT32 partition for the TrueCrypt program files and what else you may need unencrypted, and the remainder with one large, unformatted partition) and then use TrueCrypt to "create a volume within a non-system partition/drive". (Supported since version 5 of TrueCrypt.)
That way, you can't loose your TC container, except physically or by using fdisk or other partitioning software (GParted & Co.).
With the amount of times i lose my thumb drive, this doesn't look like that bad of an idea.
>> Hate to respond to my own post, but there is a way to partially protect against keyloggers -- see the section on keyfiles in the TC documentation.
What is less clear to me is, what good would a keyfile do on a removable USB stick? If the keyfile is stored on the stick, then knowing the passphrase is enough to unlock the contents. If not (e.g. it's stored on a user's desktop at home), then you can't decrypt the contents anywhere but at home, which sort of defeats the purpose of having a removable USB drive.
Can anyone shed some light on this?
/HJ
In some/most password safes, you can specify a passphrase and a keyfile, so I do both, I just create a hidden directory that looks like a program directory (AppData or something) and name is something that won't draw attention (appdata.kfl or something). I make it .kfl, so I won't forget it's a keyfile.
FYI - if you want your encrypted file to be more than 4GB you have to format the drive to NTFS. My pen drive was originally FAT32. Just google "HOW TO MAKE PEN DRIVE NTFS" and you can find your srticle of choice on how to convert it. Cheers.
First of all I would like thank you a lot for this awesome tutorial for encrypting a USB drive. And it was really easy for a newbie like me in these types of techniques. But I have a little concern.
First I would like to know how to make the data.tc file delete proof because if my usb drive is stolen all the data in the data.tc can be areased simply by pressing delete. I would like to make it very hard to be deleted unless the right authentication or even impossible to delete data.tc itself.
And second I would like to know how can I run truecrypt when I don't have administrator privilages because it won't let me unless I'm the admin and in some cases I'm not .
Please explain in an easy way and detailed because I'm new to these techniques
Thanks alot
Keith
Post a Comment